Create your own CA with TinyCA2 (part 3)
In this final part we will add our own root CA certificate to Ubuntus pre-installed certificates. (Part 1, Part 2)
Copy your root CA certificate, that we exported in the previous part, to /usr/share/ca-certificates/. Add the file name to /etc/ca-certificates.conf and run the command:
sudo update-ca-certificates
Most of your services will now be able to find your root CA certificate.
To bring your root CA certificate to your friends, just copy the exported root certificate-file to a USB-memory.
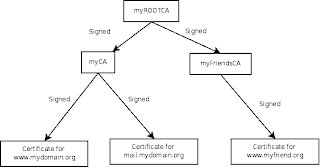
Using your own CA you can now add support SSL to different services like CUPS, postfix(AUTH SMTP), dovecot (IMAP) etc. You can also create certificates to sign and encrypt your e-mails.
Copy your root CA certificate, that we exported in the previous part, to /usr/share/ca-certificates/. Add the file name to /etc/ca-certificates.conf and run the command:
sudo update-ca-certificates
Most of your services will now be able to find your root CA certificate.
To bring your root CA certificate to your friends, just copy the exported root certificate-file to a USB-memory.
Using your own CA you can now add support SSL to different services like CUPS, postfix(AUTH SMTP), dovecot (IMAP) etc. You can also create certificates to sign and encrypt your e-mails.
Comments
1. copy
$ cp %{ROOT_CERT}.pem to /usr/share/ca-certificates/%{ROOT_CERT}.crt
(without the crt-prefix the certificate will be ignored by dpkg-reconfigure ca-certificates)
2. change rights
$ sudo chmod 755 /usr/share/ca-certificates/%{ROOT_CERT}.crt
3. update known ca-certificates
$ sudo dpkg-reconfigure ca-certificates
(you get a list of all available certificates found in /usr/share/ca-certificates, select your copied certificate)
4. verify
$ sudo ls -al /etc/ssl/certs | grep %{ROOT_CERT}
(this should output your new cert)
thanks for this superb tutorial!
thanks for this great guide.
I like it, but maybe you could tell me how to authenticate clients based on certificates.
I mean that's the point why we created a sub-ca, isn't it?
I'm looking forward for a part 4 ^^
regards Markus
Do you mean that each client should have each on certificate and that is used by the server to identify that it is an valid client? It is possible to use Sub-CA in this why but I have not done it. I use kerberos for those kind of things.
Thx,
-Adam
Now, would you know if it's secure to distribute the exported CA certificate file, by example leave it on a public part of my web site.
Would an "attacker" be able to forge new certificates from the exported CA file ?
You can for instance download my public certificate at www.linuxalert.org.
Learn more about PKI at wikipedia.
apache2: Could not reliably determine the server's fully qualified domain name, using 127.0.1.1 for ServerName
[Wed Nov 24 15:24:13 2010] [error] VirtualHost *:443 -- mixing * ports and non-* ports with a NameVirtualHost address is not supported, proceeding with undefined results
httpd (no pid file) not running
apache2: Could not reliably determine the server's fully qualified domain name, using 127.0.1.1 for ServerName
[Wed Nov 24 15:24:23 2010] [error] VirtualHost *:443 -- mixing * ports and non-* ports with a NameVirtualHost address is not supported, proceeding with undefined results
(98)Address already in use: make_sock: could not bind to address 0.0.0.0:443
no listening sockets available, shutting down
I assume the problem is that a line in apache config files is missing saying Listen *:443 and that will solve the problem.